Who Is Being Targeted

Banking Sector, Govt Agencies
Retailer, e-Commerce

Financial & Legal Services
Pharmaceuticals & Bio Technologies

Communication

Education industry

Manufacturing & Mining Industry
Any person who is using digital device like Mobile/Laptop/Tablets/Smart home/E-Cars
Who Is Being Targeted
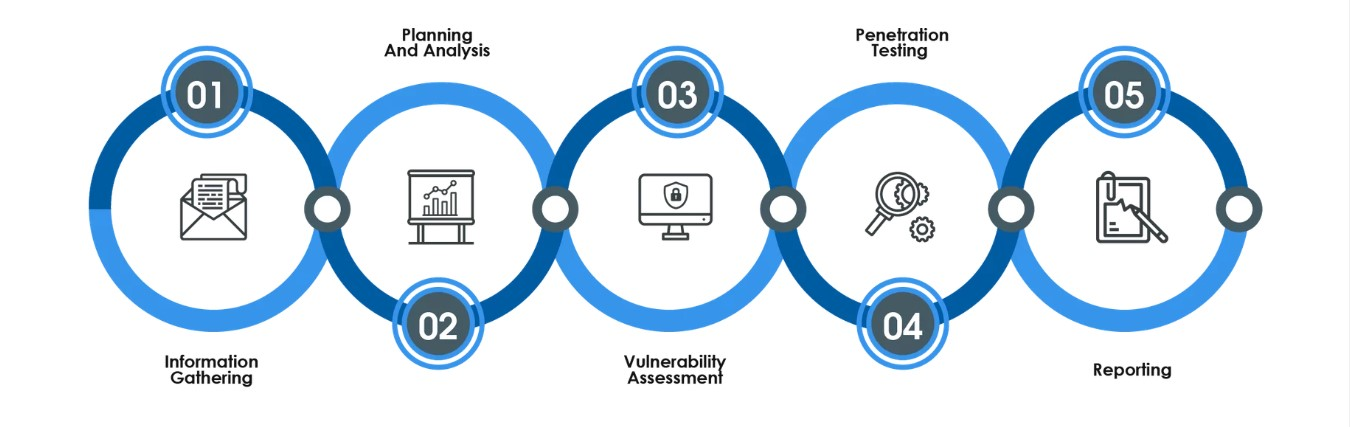
VAPT :
Vulnerability Assessment and Penetration Testing (VAPT) is a testing process to find security bugs within a software program (web/mobile) or a computer network. VAPT is often misunderstood as two different types of testing techniques. Conversely, these two should be combined together to yield better results. The objective of Vulnerability Assessment is entire to search and find bugs. Penetration Testing is performed to see whether the vulnerability exists by exploring and exploiting the system.
How do I know if my organization requires a Vulnerability Assessment? :
The necessity of Vulnerability Assessment and Penetration Testing is usually disregarded by organizations; on the contrary every organization is a potential target for hackers. This is clearly evident after recent ransomware attacks. Take responsibility and make sure proper security initiatives are taken to protect your application/data. The best practice is to conduct a Vulnerability Assessment annually or after making substantial changes to your application.
Benefits Of VAPT
When it comes to security, VAPT offers excessive benefits to an organization, let’s look at a few of its benefits.
- Provide risk management
- Align your application with Cyber Security Norms.
- Secures applications from internal and external attacks
- Protects the organizations data from malicious attacks
- Safeguards the business from loss of reputation and money
- Help the organization in identifying programming errors that lead to cyber-attacks.
- Providing the organization a detailed view of potential threats faced by an application.
VAPT Approach
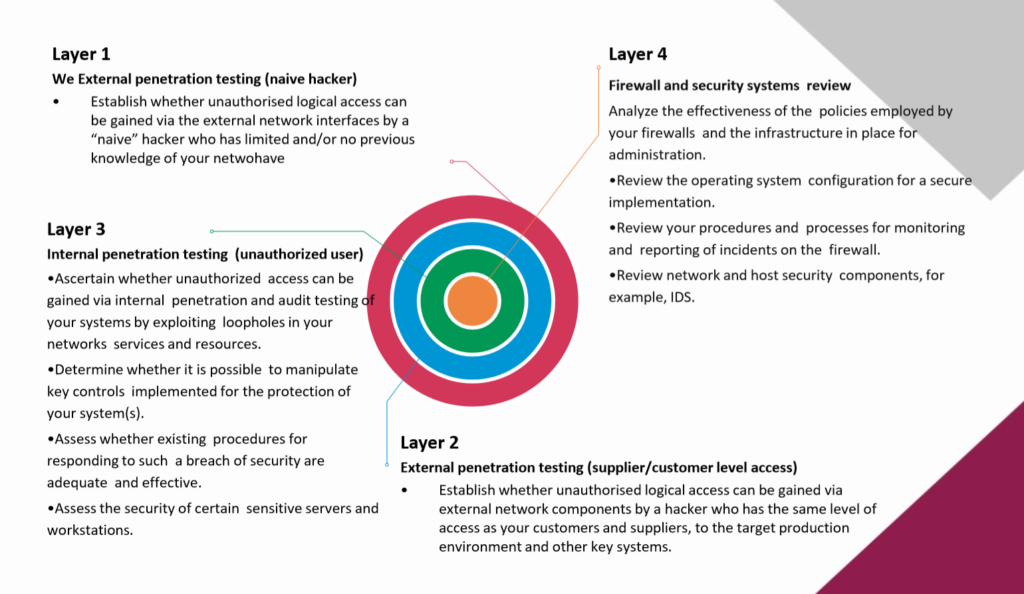
Understanding The Environment :
We evaluate the operating environment and business specific risks which enables us to focus our efforts on the areas that may represent most significant risk to the organization. We base our understanding of the environment on information supplied by the client and perform our risk analysis by means of:
- Review of existing risk analysis documentation
- Video call or Session with risk owners or their representatives
In this stage, we also agree with the client the risk rating and risk domains. Typically, these are technical risk, business risk and regulatory risk.
Testing & Initial Analysis :
Actual security testing is performed to identify risk and issues using the relevant methodologies. Efforts are focused on potential risk areas identified in earlier stages and appropriate tools and techniques are utilized accordingly. We also report identified issues along with their initial technical risk evaluation on issues that may require clients’ immediate attention using our Rapid Reporting approach.
VAPT Approach
Analyze & Recommendation :
In this stage we perform the business impact analysis of identified issues using the rating and domains agreed in the first stage. Each issue is triaged according to its urgency, and actionable based on its short, medium or long term recommendations. A root cause analysis is performed to identify the root cause of each issue in an attempt to discern if it was a single failure of the organization’s processes and procedures or if it is a more systemic issue that requires process improvements.
Typically, the deliverable of a security test is a formal report which describes in detail the work performed, results and recommendations. All reports are written for multiple audiences:
- Senior management is provided to the-point summary in easy to understand business language along with strategic recommendations if applicable.
- Staff responsible for actual remediation is provided with detailed and technical description of issues as well as specific recommendations on how to address identified risks./li>
- Middle management and line management are provided with aggregate diagrams and figures, such as heat maps, enabling them to quickly prioritize remediation actions. Strategic and tactical advice for security improvement is also provided.
VAPT Approach
Vulnerability Assessment :
Vulnerability assessment is the process of identifying and classifying the vulnerabilities with the Servers, computers and networking infrastructure. This activity helps the organization to understand the current security posture of the organization.
Activities covered:
- Network Enumeration
- Database Assessment
- Wireless Assessment
- OS patch assessment
- Web Application Assessment
- Internal Vulnerability Assessment
- External Vulnerability Assessment
VAPT Approach
Penetration Testing :
Penetration testing or pen testing is the real-world simulation attack on the IT infrastructure of the organization to gain unauthorized access to the system and network. The main difference between Vulnerability assessment and Pen testing is that VA is done using tools however PT requires manual exploit.
Activities covered:
- Social Engineering
- Server exploitation
- Network Exploitation
- Web application exploitation
- External Information gathering
Web & Mobile Application Security Assessment
We use manual and automated testing approach for this assessment.
Web and Mobile App Sec is a security assessment for websites and mobile applications. In mobile application, we test both, android and iOS.
- Source code Review
- API security assessments – REST and SOAP API
- IOS application security assessment – Static & Dynamic
- Android application security assessment – Static & Dynamic
- Web application security assessment – Black-box, Grey box & White-box testing
PS – All the above assessments are performed using principles of OWASP and SANS
Network And Systems Testing Approach
We have designed an approach that identifies the most serious risks and security flaws first and then focuses on less obvious areas as the project proceeds. First we test the network for vulnerabilities from the outside. Initially, we will conduct this test assuming the point of view of an uninformed attacker. We then gradually move on until we assume the role of a trusted user of the network trying to access an unauthorized resource or service. The following list gives some more detail as to the specifics of each level.
The consistent deployment of this approach is ensured by the use of cutting edge technology and our policy to only use highly specialised staff that work in this area with the use of comprehensive work-programmes to enhance our quality control procedures.
VAPT Layer 1, 2, 3, 4 Approach
Web Application Security Testing
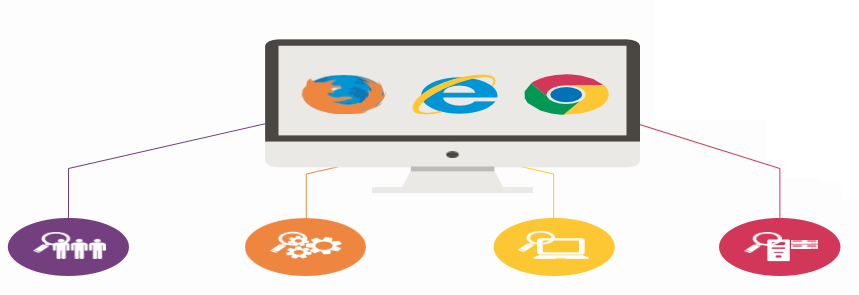
The User :
- Phishing
- Data governance
- Waterhole attacks
- Social engineering
- Update management
- Administrative access
- Password management
The Application :
- Zero-day exploits
- Brute force attacks
- Cross-site scripting
- Vulnerable libraries
- Privileges escalation
- Weak input validation
- Password management
- Weak session management
The Browser :
- Framing
- Phishing
- Click jacking
- Data Caching
- Buffer Overflow
- Man-in-the-Browser
The Backend :
Web Server:
- Cross-site scripting
- Brute force attacks
- Weak input validation
- Platform vulnerabilities
- Server misconfiguration
- Cross-site request forgery
Database :
- SQL injection
- Data dumping
- Privileges escalation
- OS command execution
Mobile Application Security Testing
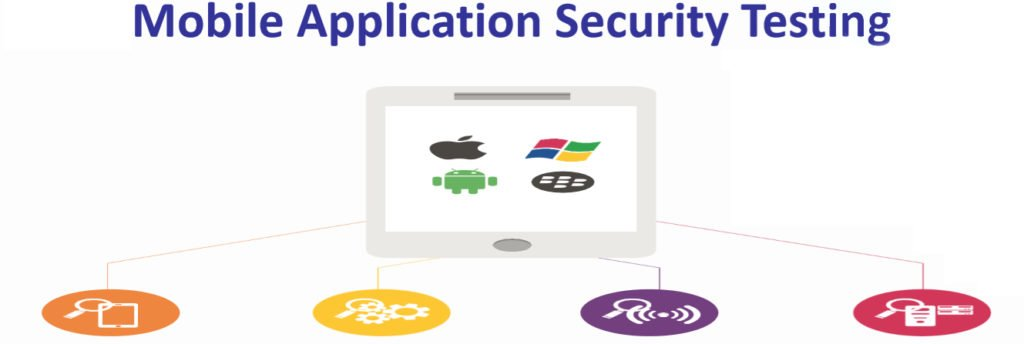
The Device :
Browser :
- Phishing, Framing, Click jacking, Man-in-the-Mobile, Buffer Overflow, Data Caching
Application :
- Sensitive data storage
- No / Weak encryption
- Improper SSL validation
- Configuration manipulation Run-time injection, Privileges escalation, Device access
Phone / SMS :
- SMS phishing
- Base-band attacks
The System :
Operating System :
- Data access
- OS data caching
- Zero-day exploit
- Jail breaking / rooting
- Password management
- Carrier-loaded software
The Network :
Communication Channels :
- Packet sniffing
- DNS poisoning
- Session hijacking
- Man-in-the-middle
- Rogue access point
- Fake SSL certificate
- No / weak Wi-Fi encryption
The Backend :
Web Server:
- Cross-site scripting
- Brute force attacks
- Weak input validation
- Platform vulnerabilities
- Server misconfiguration
- Cross-site request forgery
Database :
- SQL injection
- Data dumping
- Privileges escalation
- OS command execution
Network & Systems Testing
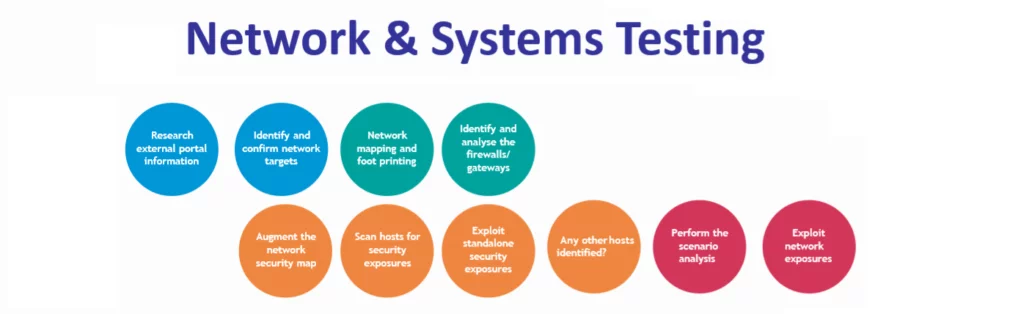
Retrieve and document information about your organization and systems from:
- The Web
- other Relevant Sources
- The Domain Name Service (DNS)
- The Internet registration database (RIPE)
- Bulletin boards, forums and other social media
Identify and analyze the front-end router for:
- Active ports
- SNMP & Finger (if active)
- Supported routing protocols
- Login ports for remote access
Identify and analyze the firewall by:
- Identifying all active TCP ports
- Identifying all active UDP ports
- Establishing the security rule base
- Testing for known security flaws
Iteratively identify and analyze accessible machines in front of and behind the firewall, which can be identified as a host using the following tests:
- Has an active TCP session established
- Has an active UDP port identified
- Test for known security flaws
Iteratively identify and exploit vulnerable systems using:
- Design errors
- Configuration errors
- Public vulnerability information
Conduct a series of scenario analysis over the entire network to establish:
- What security exposures can be exploited on the target systems.
- What unauthorized traffic can be passed to the local area network (LAN)



