We are a leading cybersecurity & solution provider In australia
Answering the Challenges facing today’s CISO
“For large, cloud-based workload deployments, cloud security
posture management capabilities should be considered mandatory.”
PRIVATE CLOUD
OUR HOLISTIC APPROACH TO ENDPOINT SECURITY IS THE ANSWER
KEY FEATURES
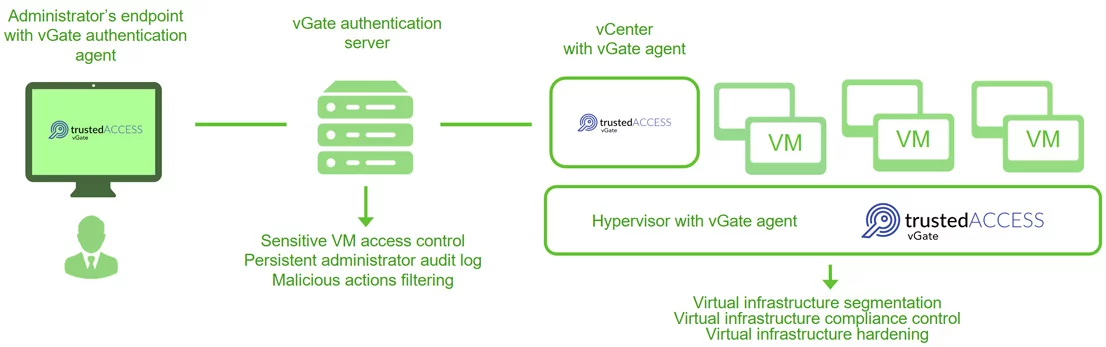
Evasion resistant audit log
Prevent hacker from covering his tracks in private cloud
management. Administrator activity logs are stored far behind
their reach. It simplifies incident forensics and remediation.
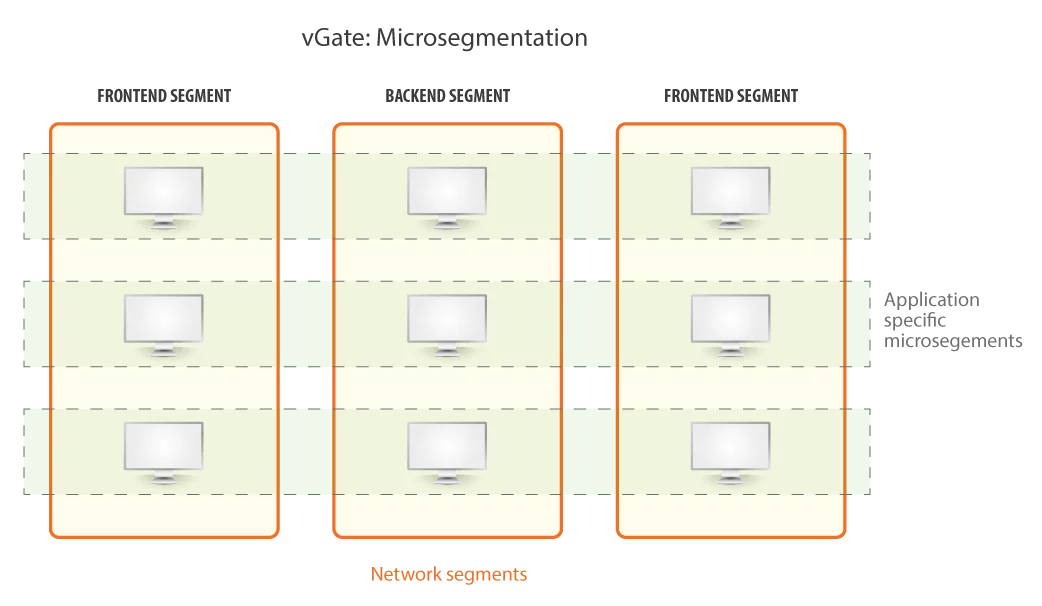
Granular Microsegmentation
Virtualization-native network access policy engine allows you to
instantly enforce and update network protection policy around your
virtual network without affecting network topology.
Virtual machine datastore protection
Unique access control mechanism protects sensitive virtual machine
data store from unauthorized access and downloading sensitive data
to Admin’s endpoint.
USE CASES
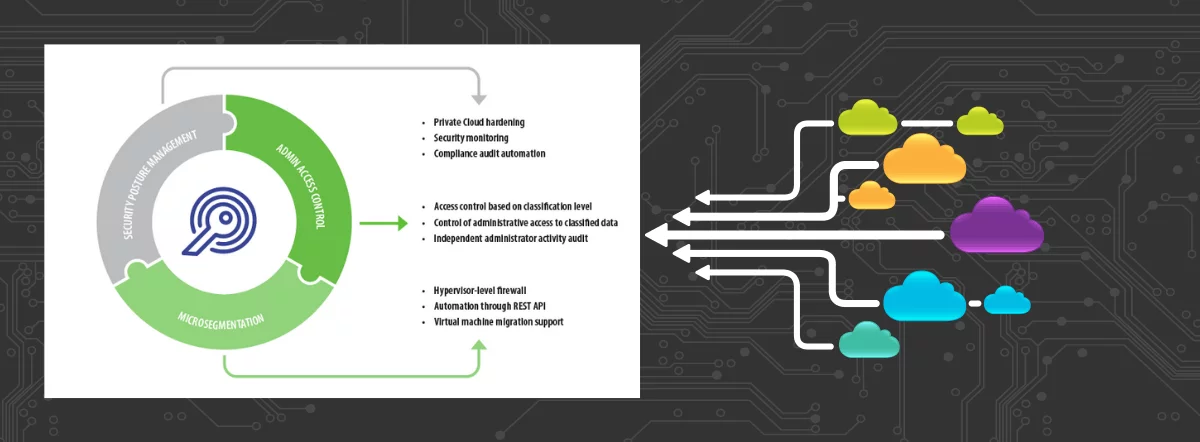
SECURITY POSTURE MANAGMENT
Approach
Virtual machine security and access control
- Snapshot restriction
- Clone restriction
- Storage data wiping
- Device contro
Hypervisor hardening :
- Host Lockdown mode enforcing
- USB drive mount restriction
- Host SSH restriction
- VM log restriction
- Host application whitelisting
- Segregation between management and production networks
Security monitoring :
- Hypervisor, management server and vGate event correlation
- Single pane of glass dachboard
Reports :
- Configuration changes
- Non-work hours access
- Most active users
- VM boot statistics
- Security policy statistics
- Compliance audit
Results
- Reduced risk of private cloud-related security incidents
-
Reduced resources to prove private cloud security compliance to
auditors
VIRTUAL NETWORK MICROSEGMENTATION
Approach
Centralized management
Layer 2 firewall
Deep Hypervisor integration :
- Agentless for VM
- Policy follows VM (in case of migration to another host)
- VM could be objects for filtering rules
Managing through both GUI and API
Works with any vSwitch :
- Standard
- Distributed
- Third Party
Results
- Reduced risks of horizontal hacker propagation
- Fast VM quarantine
- DevSecOps implementation