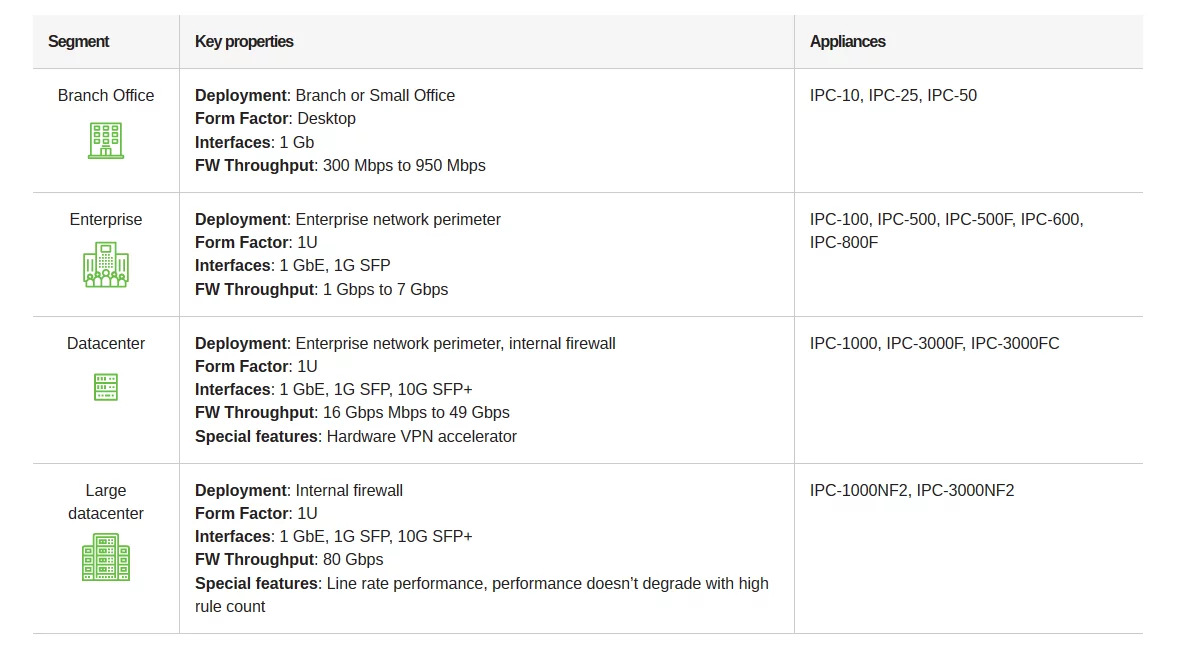
OUR HOLISTIC APPROACH TO NETWORK SECURITY IS THE ANSWER
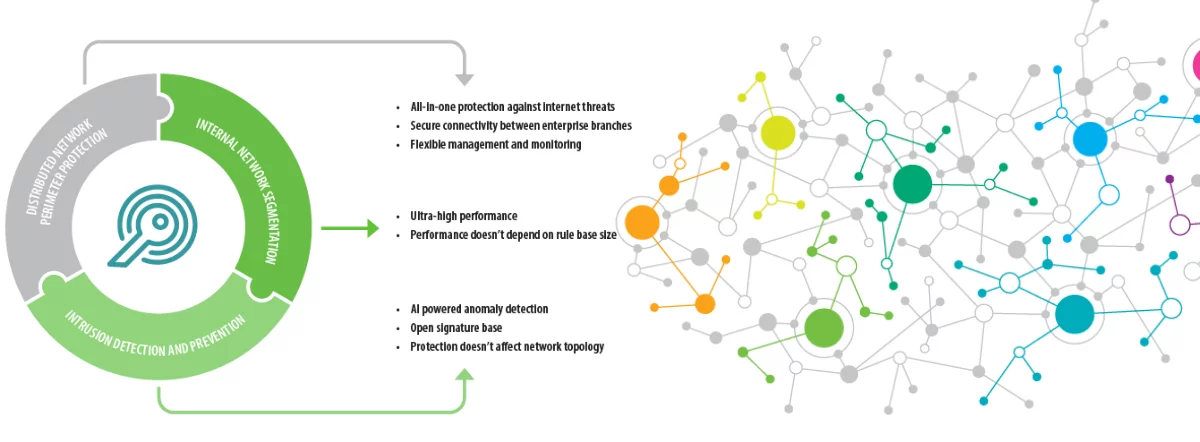
Security Through Visibility
Powerful DPI engine allows you to Identify more than 2600 applications Including Instant messaging, social media, file sharing and enterprise applications. Allow the ones you need and block the rest.
AI-Based Attack Protection
Signature-less Intrusion detection system allows you to catch adversaries inside your network. Evasion resistant technology constantly monitors network and highlights suspicious activity.
Advanced Encryption Technologies
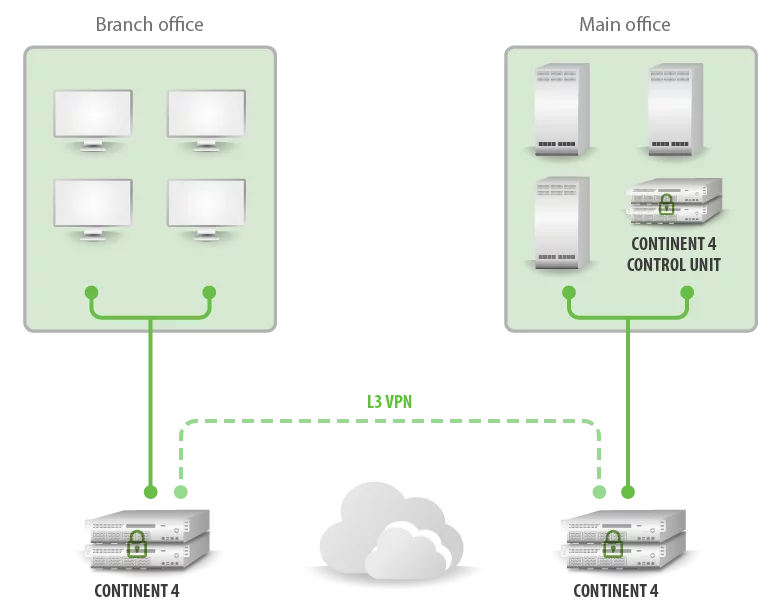
Highly sophisticated network encryption technologies provide secure connectivity between HQ and branches. FPGA based encryption module provides up to 20 Gigabits per second low latency encryption performance.
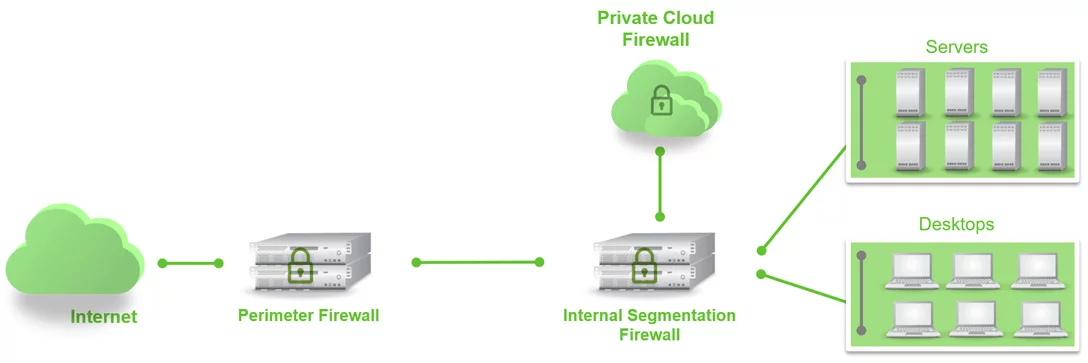
Approach
Centralized management :
Granular Identity based policy :
Flexible web- monitoring interface
Application control engine (2600 applications)
Malicious URL blocking
Network behavior anomaly detection
NAT support
Dynamic routing
Results
Approach
Automated ‘Waterfall’ to binary tree rule translation
High packet-per-second rate
Intel DPDK framework implementation
NAT support
Routing support
Results
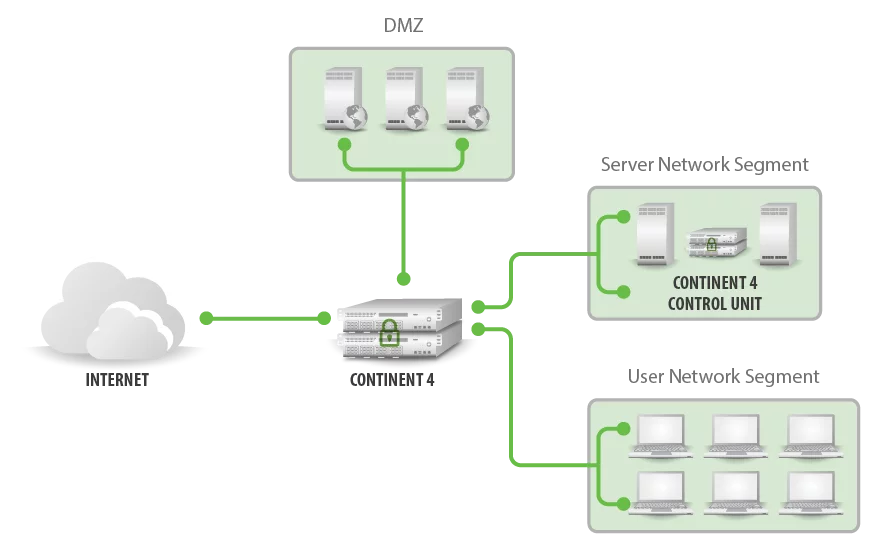
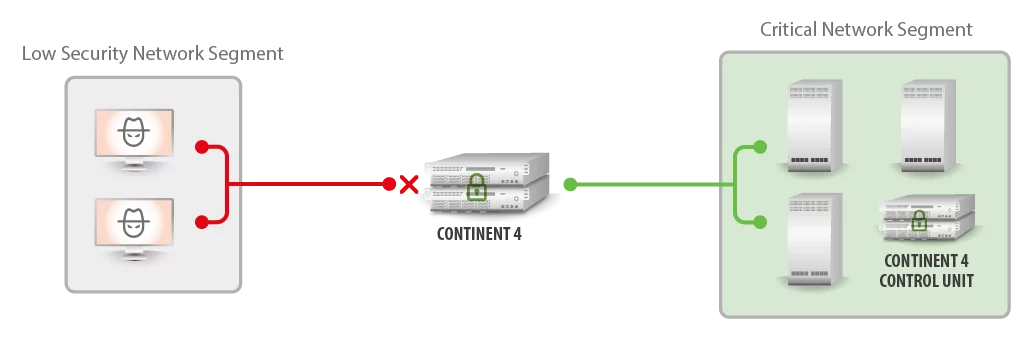
Approach
lexible signature profile settings :
Granular IPS profile enforcement
Network behavior anomaly detection :
Open signature base
Performance impact optimized signatures
Results