

Answering the Challenges facing today’s CISO
“Security and risk management leaders focused on endpoint and mobile security must choose products and technologies that blend information-centric protections into a ‘defense in depth’.”
“By 2020, more than 60% of organizations will invest in multiple data security tools, up from approximately 35% in 2017.”
Secret Net Studio
SEGREGATION OF DUTIES BETWEEN SECURITY AND OPERATIONS TEAMS
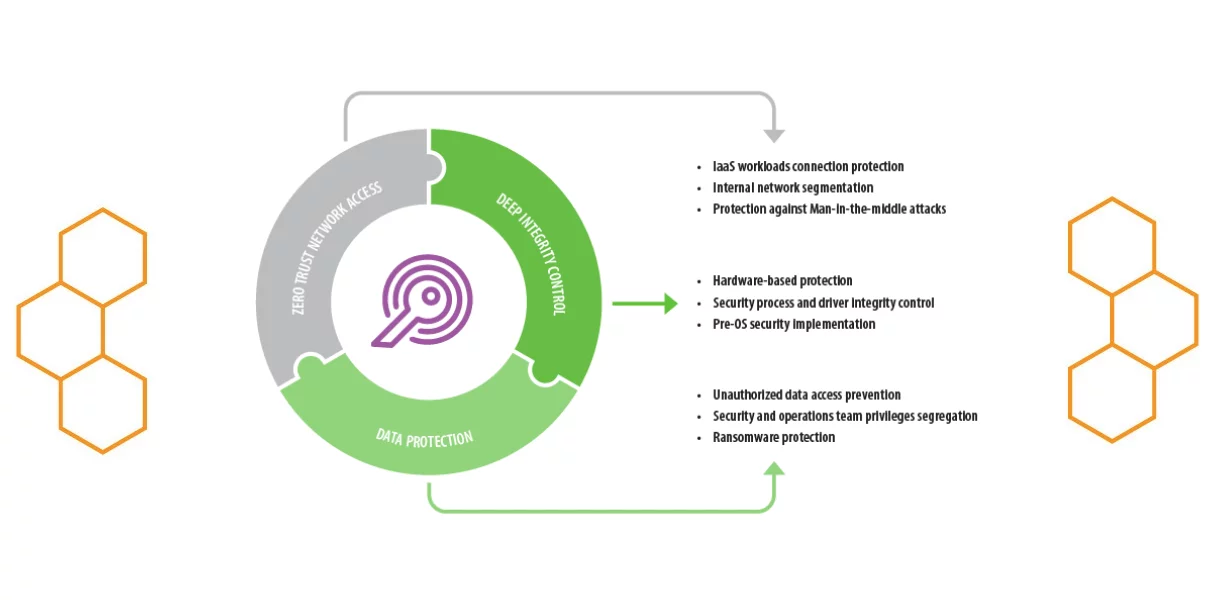
Sensitive information remains protected from anyone except its owner and designated people. Neither IT infrastructure administrators nor Security administrator cannot unauthorized change it. Unique architecture provides double access control. IT infrastructure admin cannot change the security part of policy, Security officer cannot change the infrastructure part of policy.
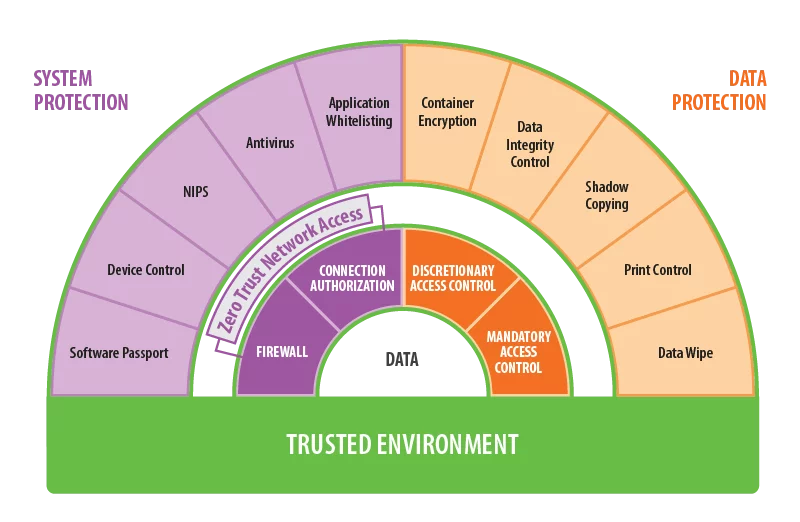
TRUSTED SECURITY MECHANISMS
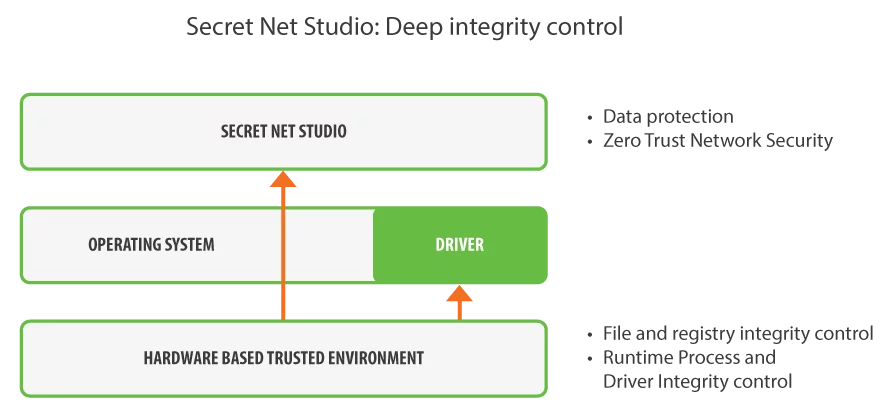
Hardware-based Trusted Environment Technology allows you to protect security mechanisms and system drivers without a hacker knowing about it. Vulnerable processes and drivers are controlled from below the operating system with software based on dedicated CPU-core and separate hardware module. These components completely invisible to adversary
SOFTWARE DEFINED PERIMETER
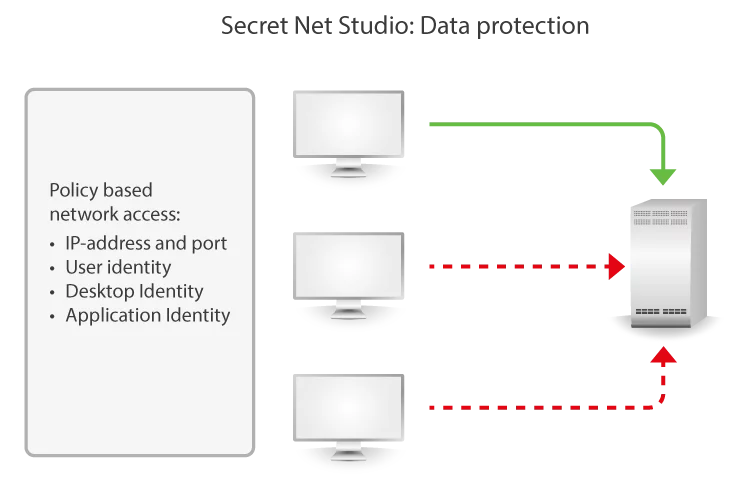
Secret Net Studio allows you to build flexible segments across internal network. Granular access policy provides zero-trust network connectivity and prevents hacker from propagation to sensitive segments. Connection is not allowed until user, application and endpoint are authorized.
CLASSIFICATION-BASED ACCESS CONTROL
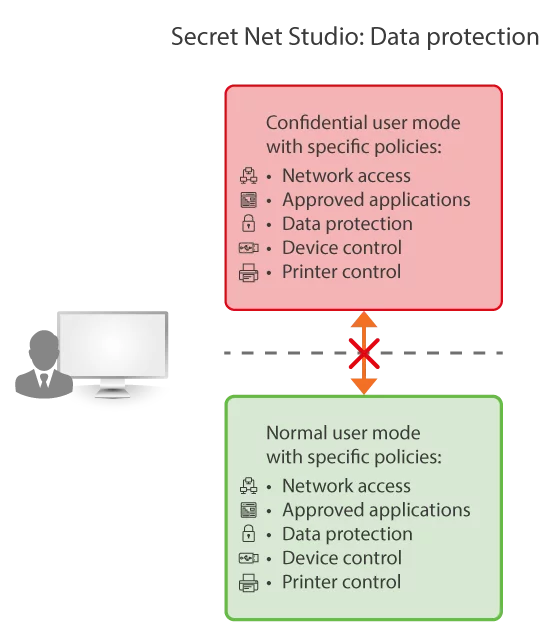
Mandatory Access Control is the core security mechanism of Secret Net Studio. It appliies to data, applications and devices. It allows you to provide data protection with analysing just classification tag instead of reading file content.
Approach
Mandatory access control for:
Context is set by:
Windows Terminal session support
Up to 16 classification policy levels
Printer access control:
Device control
File wiping
Results
Approach
Software firewall
Network connection filtering:
Application of firewall rules by schedule :
Firewall learning mode (adaptive rule whitelisting)
Secure connection :
Results
Approach
Trusted security environment on the hardware level :
Separate checksum storage :
Secure Boot :
Results